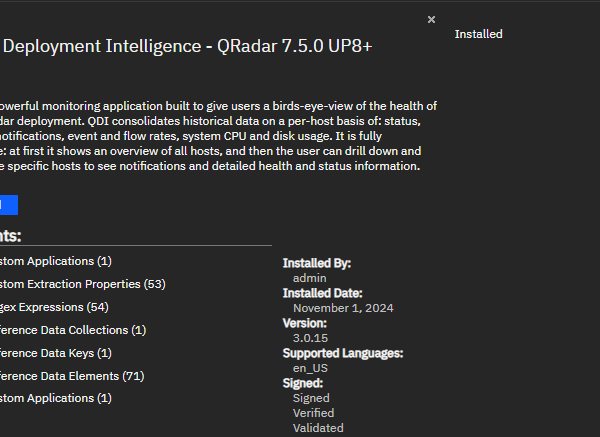
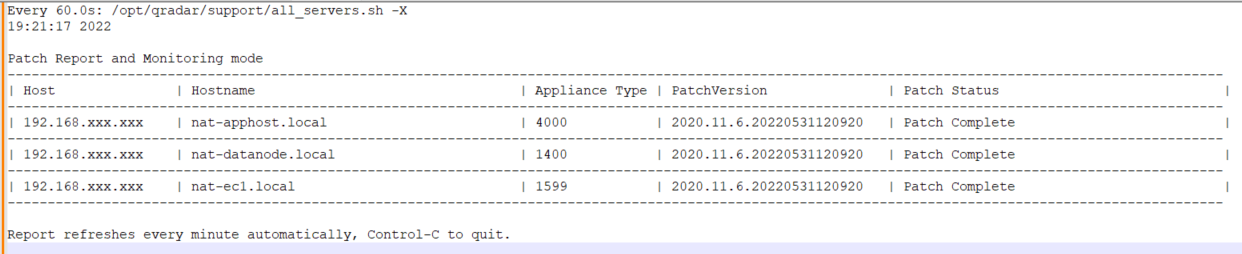
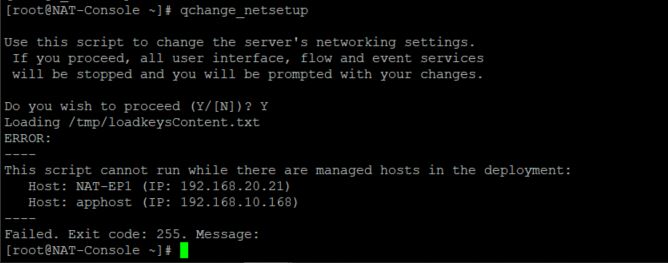
QDI app 3.0.15 release
IBM’s QRadar is a leading Security Information and Event Management (SIEM) solution, empowering organizations to effectively manage, analyze, and respond to security […]
New QRadar 7.5.0 UP10 is published
A new version of QRadar 7.5.0 UP10 was published on 14 October 2024, bringing many new features, which I will summarize in […]
QRadar upgrade – Parallel upgrade vs. Patch all
There are two methods commonly used for the QRadar upgrade. These methods apply to the distributed deployment only but not to the […]
Add new DNS servers to QRadar
There is a common problem with how to add new DNS servers to QRadar if you need to change them. Normally, you […]
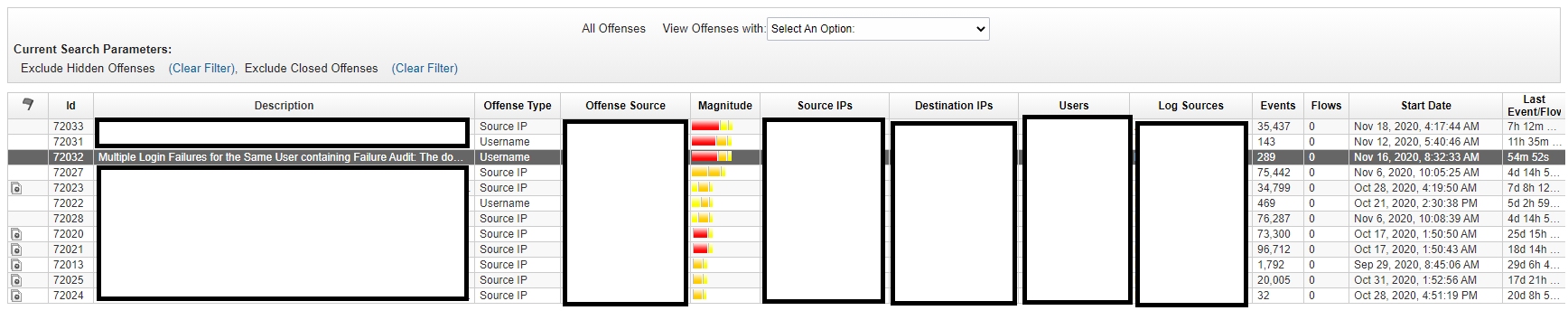
An open offense can be inactive in the Backend
An open offense can be inactive in the Backend if there are no new events that arrived for at least 30 minutes. […]
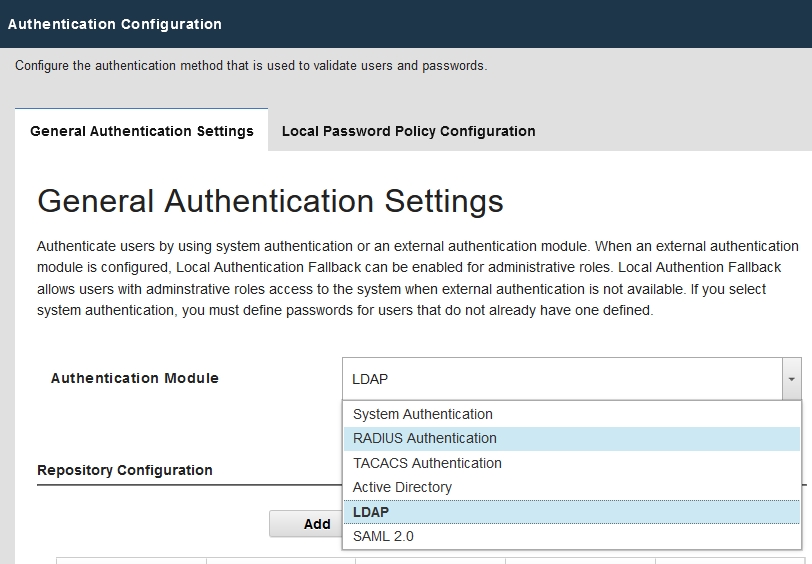
How to change a forgotten password in QRadar
QRadar has multiple ways to authenticate users. Apart from the default System Authentication based on data kept in the Postgres database, you […]
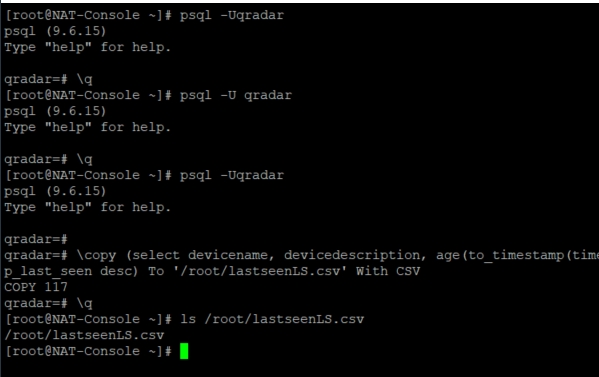
List and export all enabled Log Sources using psql query in QRadar
In order to export a list of all enabled log sources, SIEM administrators can run one of the following commands basd on […]
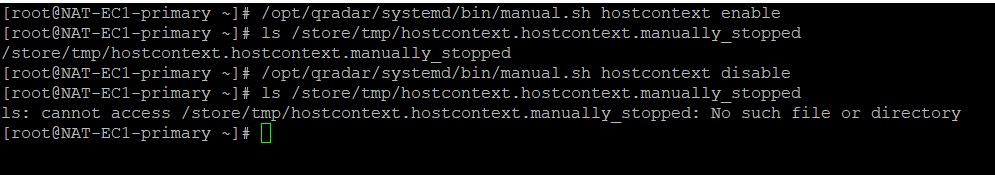
Manually stop QRadar services
Most of QRadar administrators are familiar with the command issued in the backend, which restarts services (systemctl restart hostcontext). You should know […]
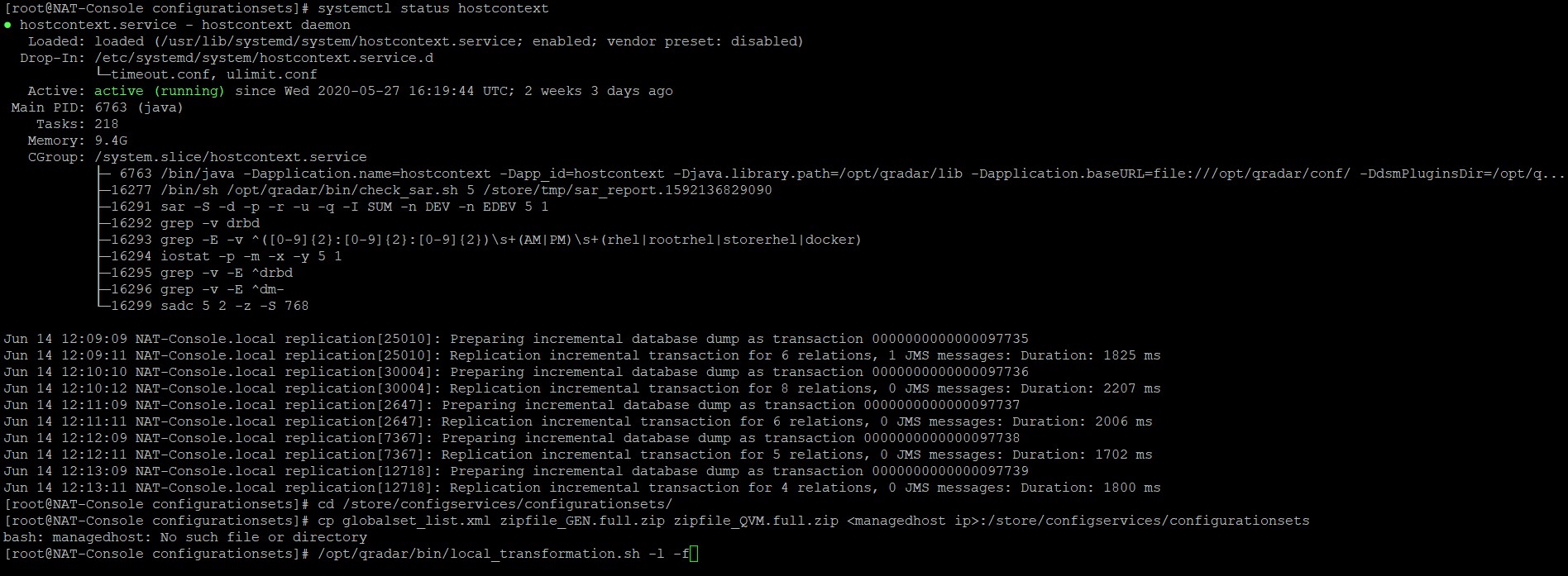
Deploying changes locally
Many QRadar users and admins hit time out or error issue when they are deploying changes in QRadar to the Managed Hosts. […]
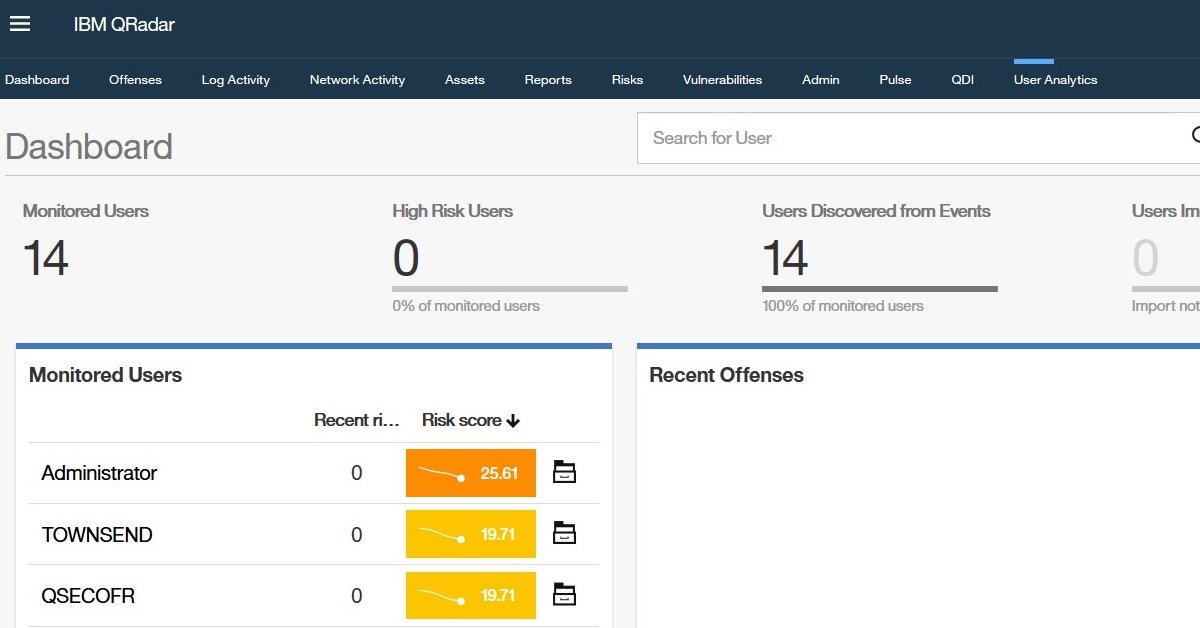
User Behavior Analytics 3.6 (UBA) with Multi-Tenancy support
It has been announced, that soon we can expect a new version of UBA extension to QRadar functionality. The new version with […]