Bad Rabbit Malware Content Pack
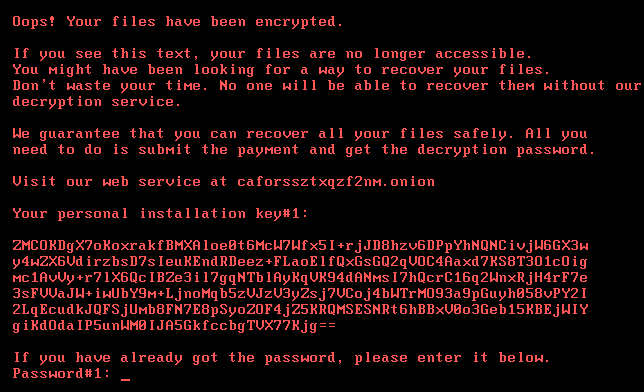
Bad Rabbit malware.
On October 24th there were found new attacks on many sites using previously unknown ransomware, which later has been called Bad Rabbit.
Bad Rabbit was distributed with the help of drive-by attacks. When the vicitim was visiting one of modified website, a malware dropper was being downloaded from the threat actor’s infrastructure. No exploits were used, so the victim would need execute the malware dropper manually, which was disguised as an Adobe Flash installer.
Once infected, the user is informed that their files have been encrypted and that it will cost 0.05 bitcoins (approximately 280 US dollars) for the key to use to decrypt them. Currently, there is no indication that paying the ransom will result in a valid key that will decrypt the victim’s files properly. The screen shot below shows a ransom message displayed on victims screen:

According to Kaspersky Lab this been a targeted attack against corporate networks, using methods similar to those used during the ExPetr attack.
Technical details
Bad Rabbit is spread via a drive-by attack. The ransomware dropper is distributed from hxxp://1dnscontrol[.]com/flash_install.php. Victims are redirected to this malware web resource from legitimate news websites like Russian Interfax and Fontanka. The downloaded file named install_flash_player.exe needs to be manually launched by the victim. To operate correctly, it needs elevated administrative privileges which it attempts to obtain using the standard UAC prompt. If started, it will save the malicious DLL as C:\Windows\infpub.dat and launch it using rundll32. There is also found file called infpub.dat appears to be capable of brute-forcing NTLM login credentials to Windows machines that have pseudo-random IP addresses. File infpub.dat will also install the malicious executable dispci.exe into C:\Windows and create a task to launch it. What’s more, infpub.dat acts as a typical file encrypting ransomware: it finds the victim’s data files using an embedded extension list and encrypts them using the criminal’s public RSA-2048 key.
The executable dispci.exe appears to be derived from the code base of the legitimate utility DiskCryptor. It acts as the disk encryption module which also installs the modified bootloader and prevents the normal boot-up process of the infected machine. An interesting detail that was noticed, when analyzing the sample of this threat: criminals are fans of Game Of Thrones.

As mentioned, the Bad Rabbit ransomware encrypts a victim’s files and disk. Files are encrypted with the following algorithms:
AES-128-CBC
RSA-2048
It is a default encryption scheme for ransomware.
An interesting fact is that the ransomware enumerates all running processes and compares the hashed name of each process with embedded hash values. It is important to mention that the hashing algorithm is similar to the ExPetr one.
The full list of embedded hashes of process names:
| Hash | Process name |
| 0x4A241C3E | dwwatcher.exe |
| 0x923CA517 | McTray.exe |
| 0x966D0415 | dwarkdaemon.exe |
| 0xAA331620 | dwservice.exe |
| 0xC8F10976 | mfevtps.exe |
| 0xE2517A14 | dwengine.exe |
| 0xE5A05A00 | mcshield.exe |
The partitions on the victim’s disks are encrypted with the help of the DiskCryptor driver dcrypt.sys (which is installed into C:\Windows\cscc.dat). The ransomware sends the necessary IOCTL codes to this driver. Some functions are taken as is from the sources of DiskCryptor (drv_ioctl.c), others seem to be implemented by the malware developers.
Hashes of files used in ransomware are below:
IOCs:<br>http://1dnscontrol[.]com/<br>
fbbdc39af1139aebba4da004475e8839 – install_flash_player.exe<br>
1d724f95c61f1055f0d02c2154bbccd3 – C:\Windows\infpub.dat<br>
b14d8faf7f0cbcfad051cefe5f39645f – C:\Windows\dispci.exe
Most of the attacks seen by ESET have been in Russia and the Ukraine, although there are some reports that attacks have occurred in Turkey, Bulgaria, and Germany as well.
Most of victims was found in Russia and Eastern Europe. Russian news sites Interfax and Fontanka as well as Odessa International Airport and Kiev Metro have reported an attack. Below list of known compromised sites:
argumentiru.com, www.fontanka.ru, grupovo.bg, www.sinematurk.com, ica.co, spbvoditel.ru, argumenti.ru, www.mediaport.ua, blog.fontanka.ru, an-crimea.ru, www.t.ks.ua, most-dnepr.info, rta.com, www.otbrana.com, calendar.fontanka.ru, www.grupovo.bg, www.pensionhotel.cz, www.online812.ru, www.imer.ro, novayagazeta.spb.ru, i24.com, bg.pensionhotel.com, ankerch-crimea.ru, bingo.bangabongo.org

Out of the box QRadar will detect BadRabbit Ransomware as it moves laterally, exploits vulnerabilities and communicates with non-trusted internet sources. This content pack adds additional detection based on collaboratively developed threat intelligence for higher fidelity detection.
This content pack contains:
– 4 Reference sets
– 7 Building Blocks
– 1 Custom Rule
– 4 Event Saved Searches
– 2 Flow Saved Searches
The 4 reference sets for the BadRabbit Ransomware contain IP’s, Filenames, Hashes, HostNames for the BadRabbit
Content Pack is available to download from the following link.